Microsoft Azure SSO implementation steps
Only CDD version 4.14 and Outlook Plugin version 2.9 and newer versions support Azure SSO - distributed (April 2024)
In these example we will use the following data which will be different in your case and needs to be adjusted according to domain name provided for you:
CoreData portal address (use address provided for your organization)
https://test01-dev.coredata.isConfiguration steps needed on Microsoft Azure
Create new Enterprise Application:
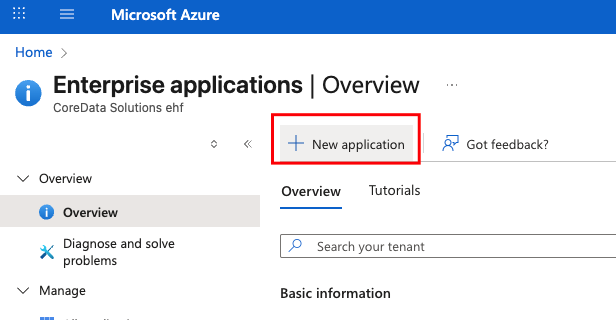
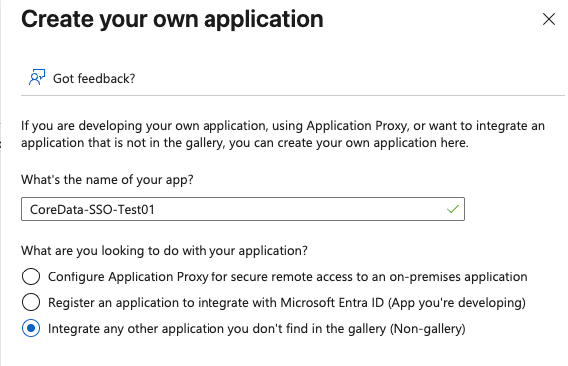
Create your own application:

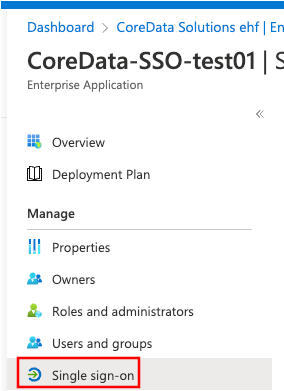
Go to Single sign-on:
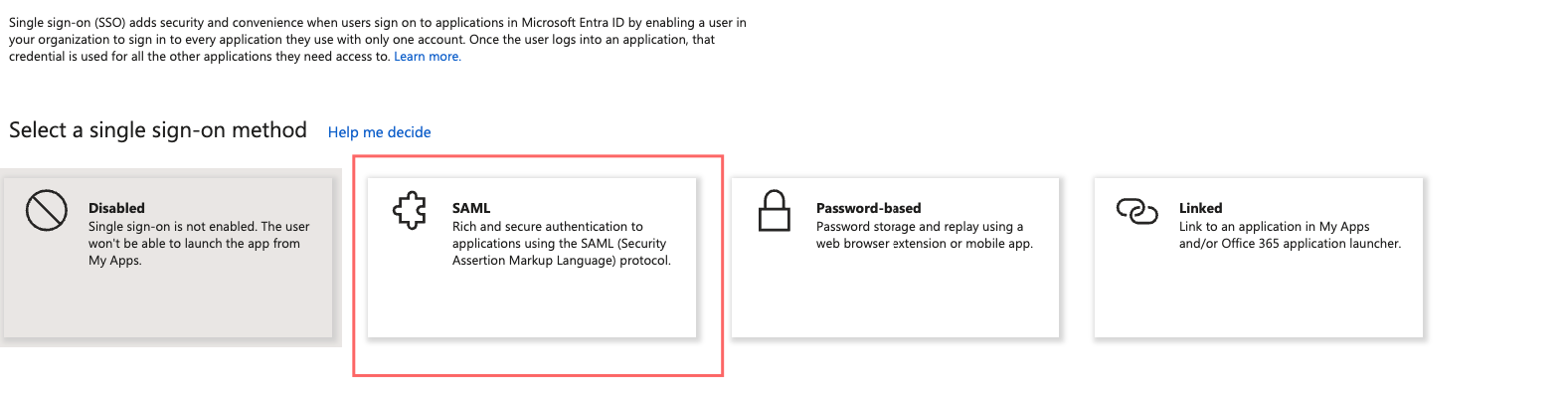
Setup Basic SAML Configuration:
Template:
Please pay ATTENTION to the slash symbol at the end - it’s important: “/”.CODEIdentifier (Entity ID) https://test01-dev.coredata.is/saml2/metadata/ Reply URL (Assertion Consumer Service URL) https://test01-dev.coredata.is/saml2/acs/ Logout Url (Optional) https://test01-dev.coredata.is/saml2/ls/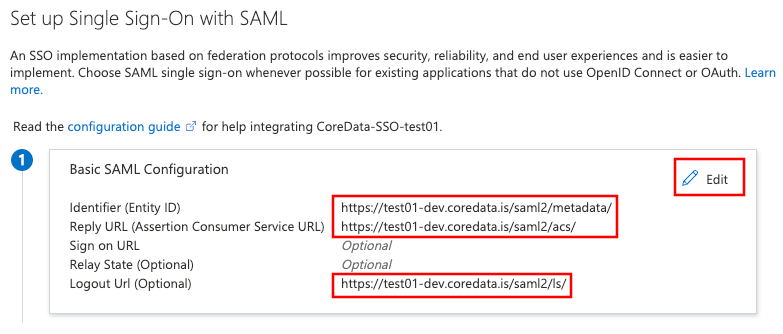
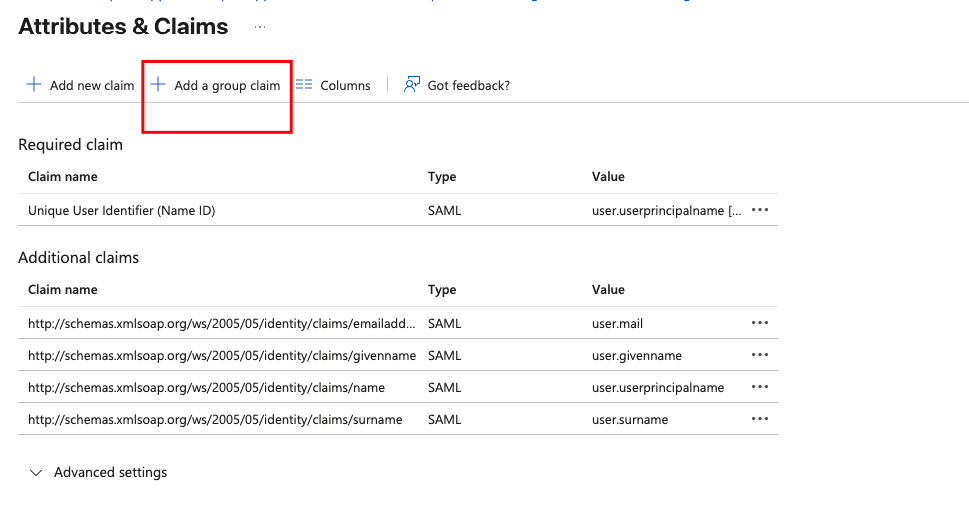
Setup Attributes & Claims:
Add group claim
user.groups custom claim setting with more details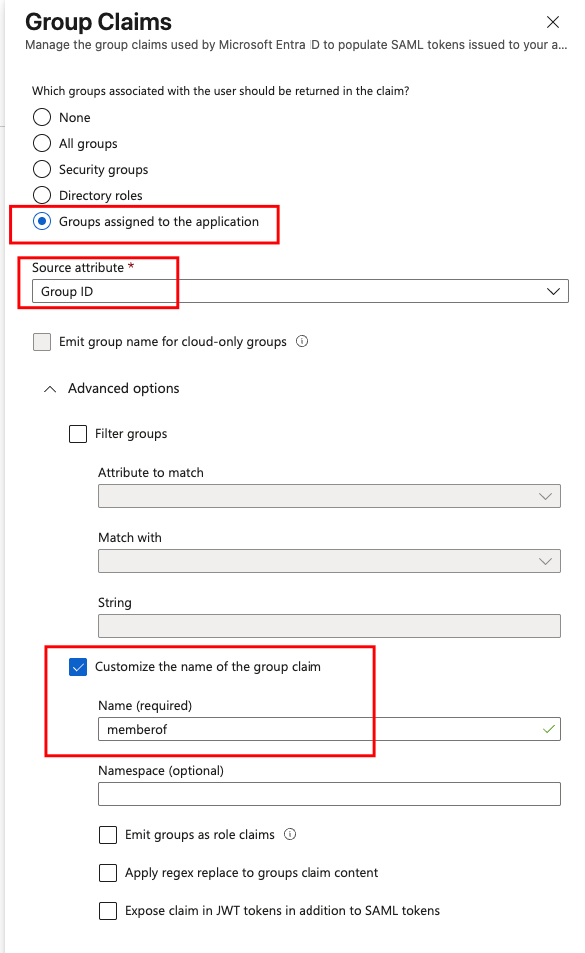
Add new Claim uid
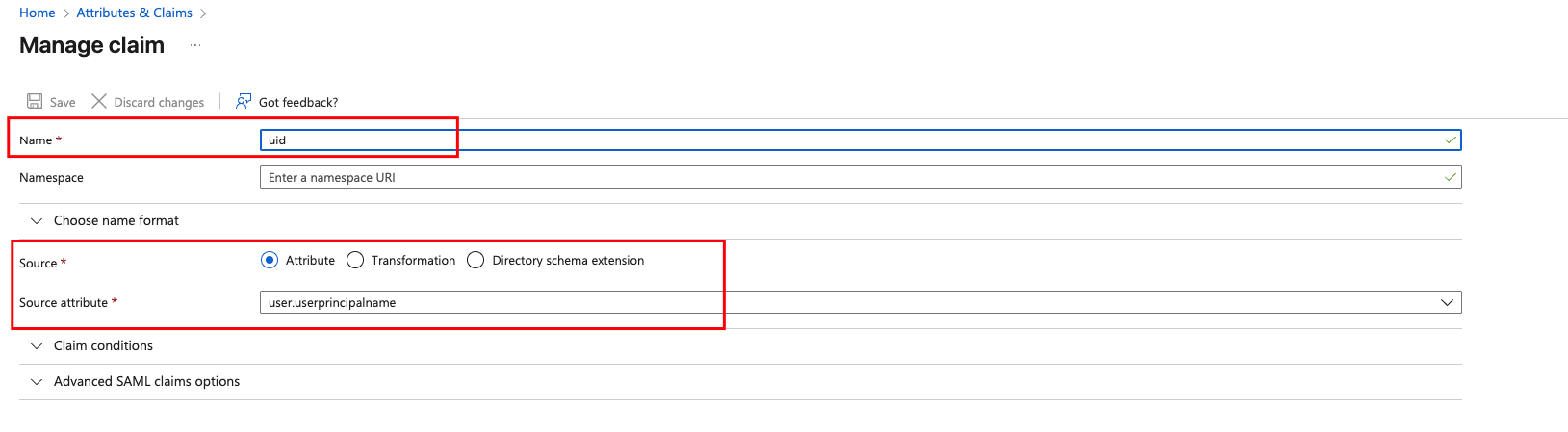
Attributes & Claims should look like this:
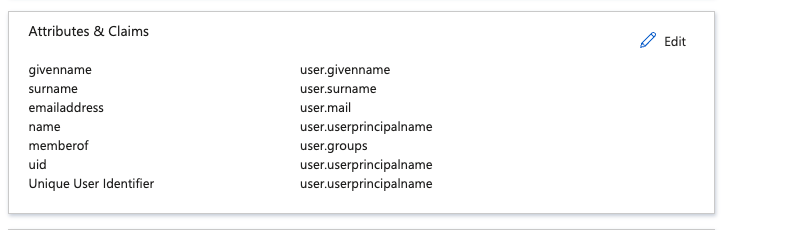
In SAML Certificates download the metadata XML. It Contains Azure public certificates. Remember that from time to time they expire. In case of any issues with SSO - please try donwloading new version from Azure and re-upload to CoreData as shown later in this guide:
Edit SAML Certificates
Chose Signing Option: Sign SAML response: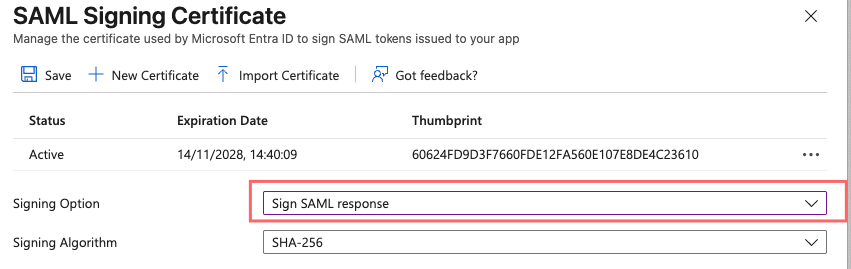
Copy the marked Login URL and Logout URL and provide it also for CoreData support:
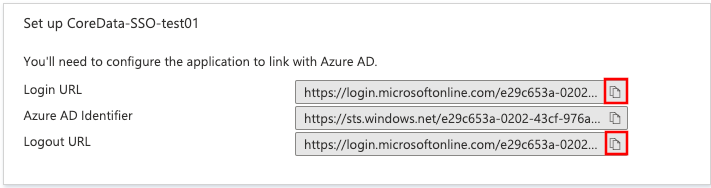
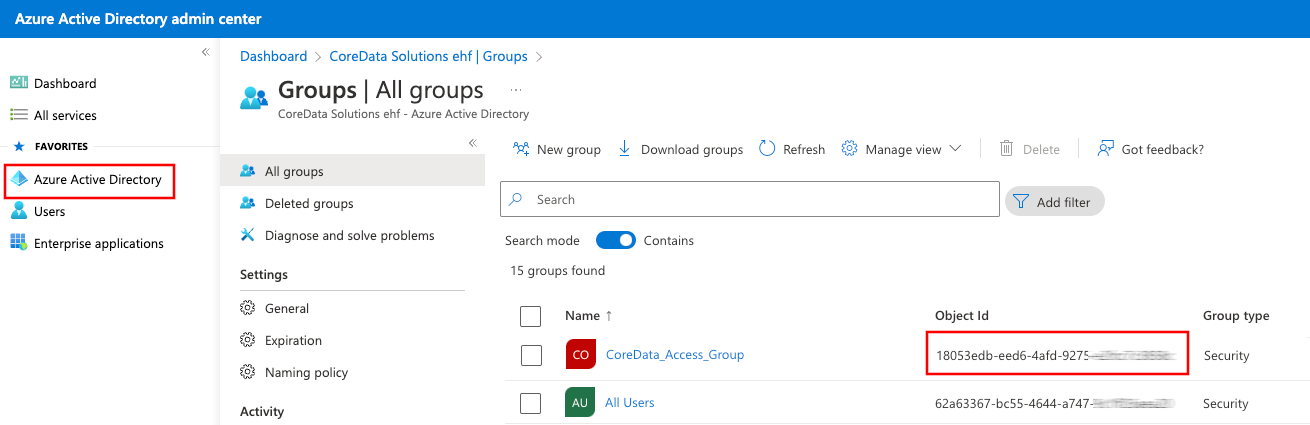
Almost done! Now you need to create if needed a new Azure Active Directory group of users who should be allowed to use CoreData. Or you can re-use existing Group. You need to provide the group Object ID for CoreData support.
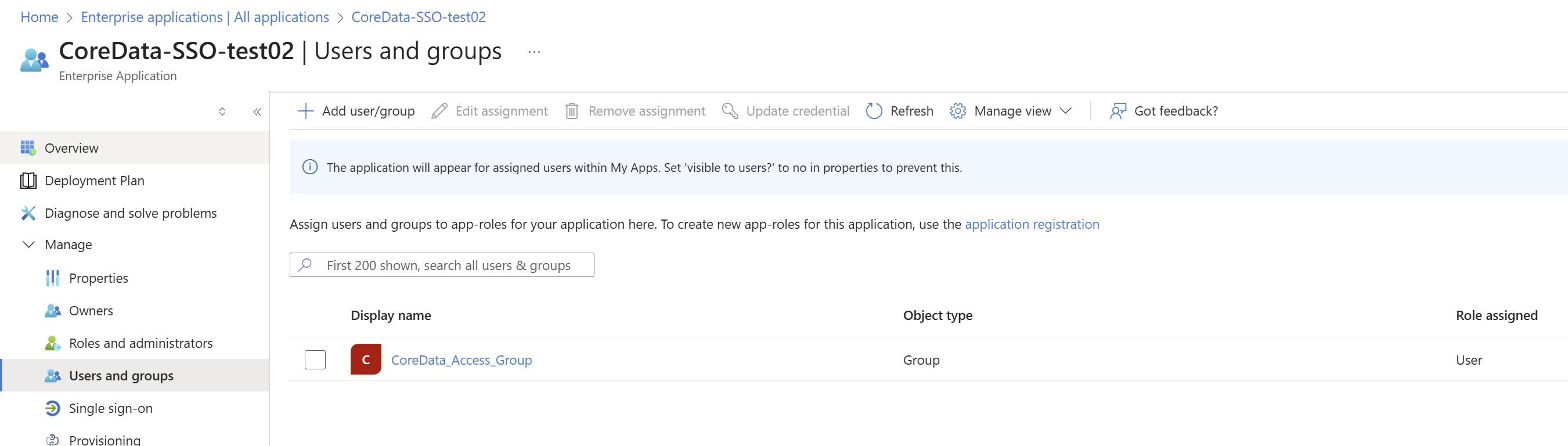
Final step is to add group under enterprise application - “user and groups”
Configuration steps needed on CoreData
Continue with these steps as one of CoreData support roles: admin_delegate or administrator when configuration is ready on Microsoft Azure. Make sure you have collected these details from Microsoft Azure cloud admin dashboard:
Login URL.
Logout URL.
Federation Metadata XML file.
Group Object ID.
Login to CoreData admin Dashboard as admin_delegate or administrator user:
Go to Security - Identification Providers
Tip: if you do not see this tab - please contact CoreData support so that SSO extension would be enabled for you.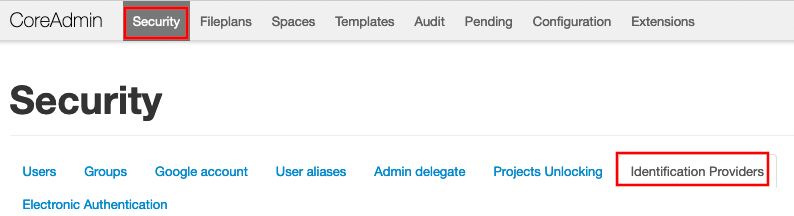
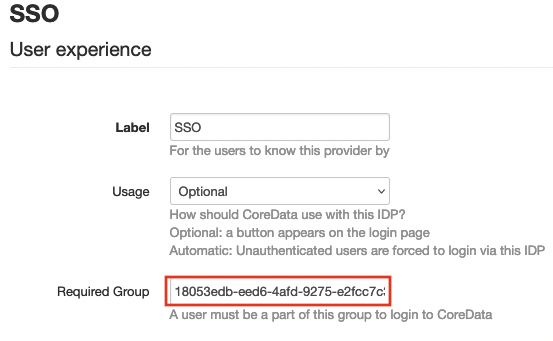
Fill in Group Object ID (Can be found on step with Azure Active Directory):
Entity ID:
Just need to put correct domain name, the remaining part of URL is the same for all deployments.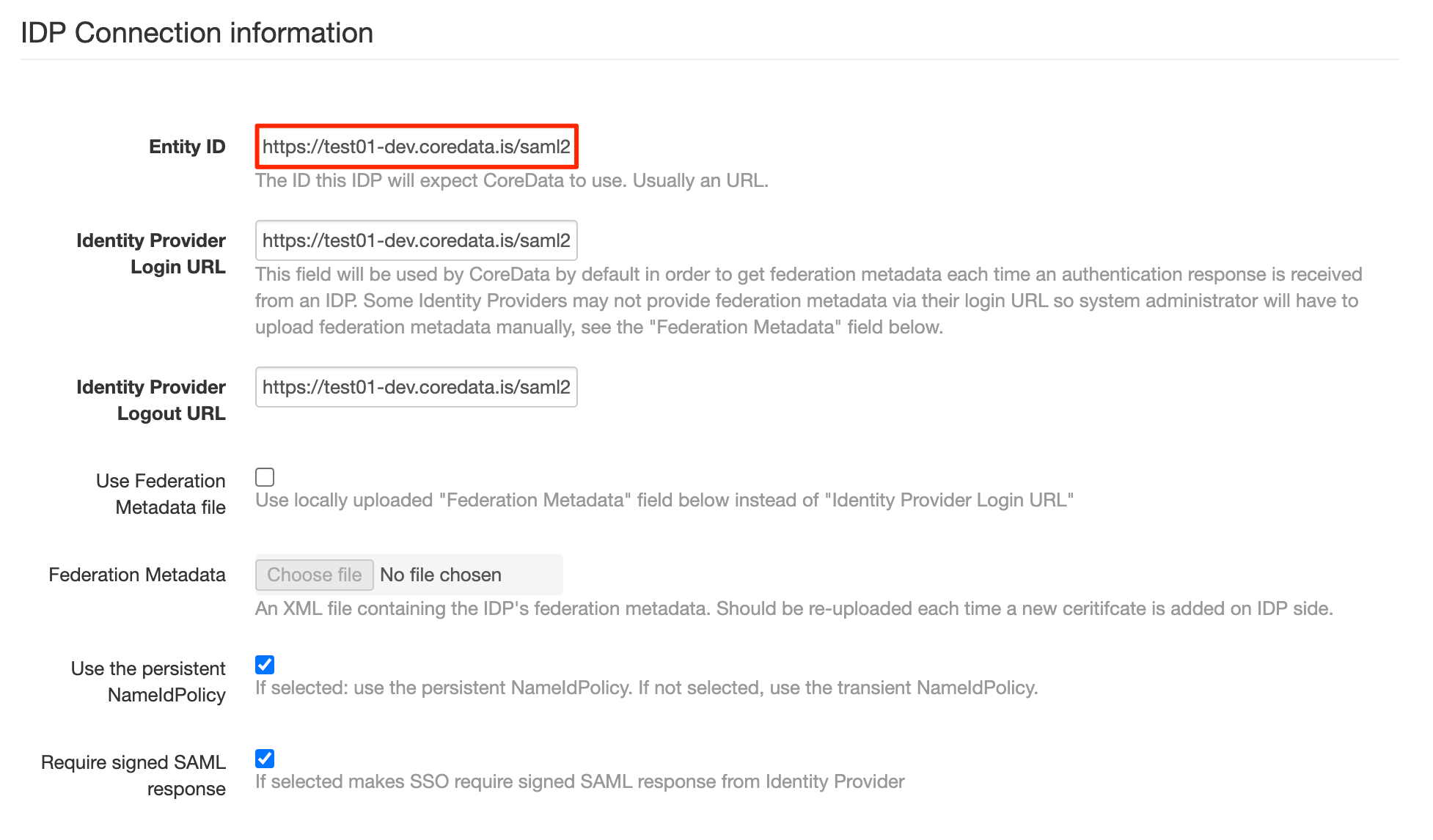
Example:
Please pay ATTENTION to the slash symbol at the end - it’s important: “/”.CODEhttps://test01-dev.coredata.is/saml2/metadata/Identity Provider Login URL
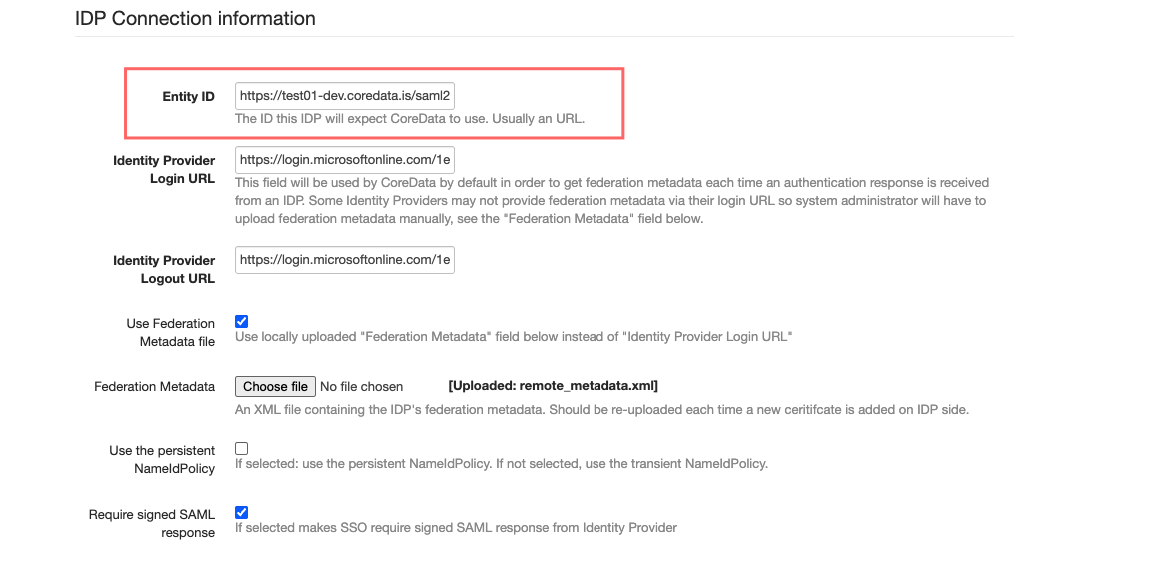
Example:CODEhttps://login.microsoftonline.com/e29c653a-0202-43cf-976a-8b0242fe7c14/saml2Identity Provider Logout URL
Example:CODEhttps://login.microsoftonline.com/e29c653a-0202-43cf-976a-8b0242fe7c14/saml2
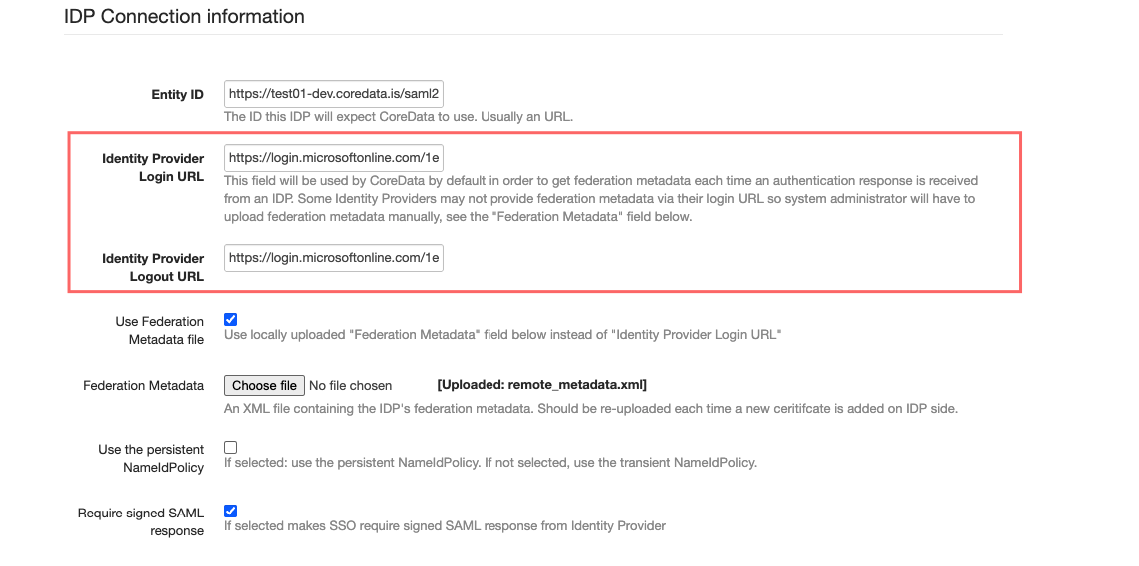
Upload metadata XML from Azure:
If you are configuring an IDP which does not provide a public federation metadata URL, then you may want to upload up to date federation metadata manually: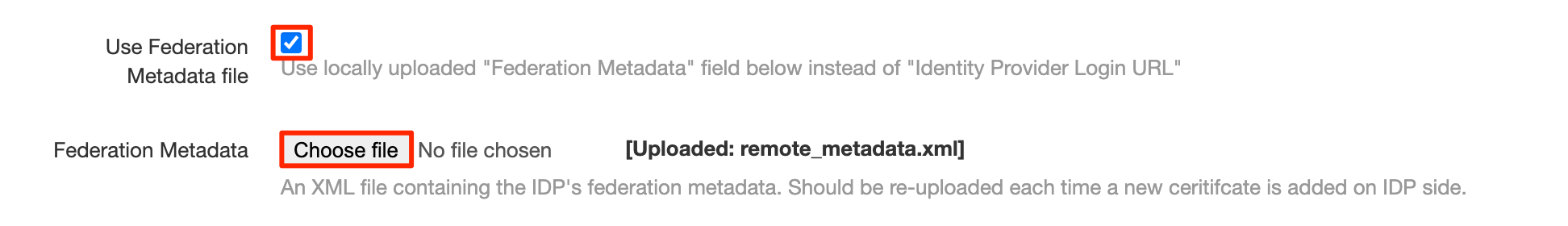
Message encryption:
Enable SAML response signature requirement:
If this enabled, please check again step 12 in azure if Signing Option “Sign SAML response” is selected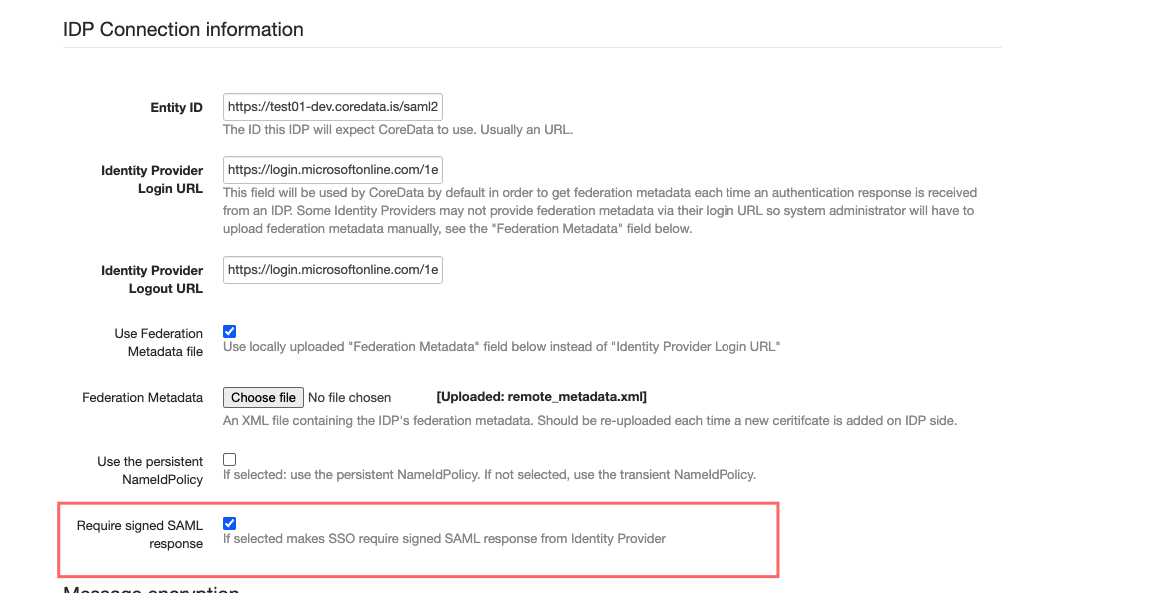
Here you can put a private and public key certificates generated using OpenSSL. These certificates can be self-signed. Or they can be issued by certificate authority. Here we will provide steps for Self-Signed.
Generate private key:CODEopenssl genrsa -out private.key 4096
Generate public key (in this example certificate will work for 2 years, remember to update because otherwise SSO functionality will stop working):CODE# Variables to set: CORE_DOMAIN="" # change this to domain which was assigned for you CORE_EMAIL="devops@coredata.is" # can change if needed # Command: openssl req -x509 -new -nodes -days 730 -key private.key -sha256 -out public.pem -subj "/C=IS/ST=Lagmuli/L=Reykjavik/O=Coredata Solutions ehf./CN=$CORE_DOMAIN/emailAddress=$CORE_EMAIL"
Upload the files.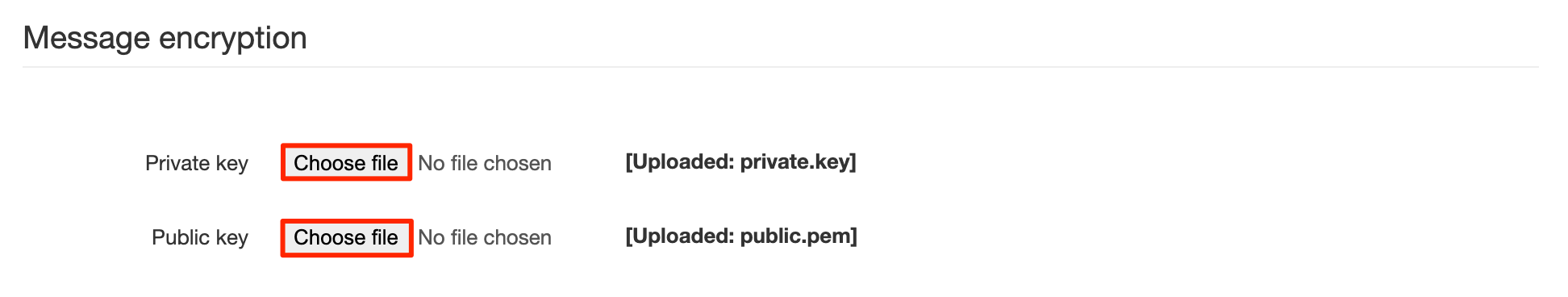
Finished. You cant test the integration by directly logging in to CoreData or by clicking from Azure Dashboard:
That should take you to CoreData.
Azure AD certificate expiration
When current certificate expires in Azure AD:
Azure AD does not create a new certificate automatically.
Azure AD does not activate the next certificate automatically.
Usually certificates expire every 2 years.
Azure AD certificate renewal
Having the information provided above here is a scenario example of how to approach an expiring Azure AD certificate renewal:
Given:
An active Azure AD certificate expiring soon.
CoreData has an up-to-date metadata XML file uploaded earlier.
CoreData SSO is configured for the given Azure AD and working properly.
System Administrator:
Receives a notification regarding the expiring certificate from Azure AD.
Creates a new inactive certificate in Azure AD. The new certificate validity period overlaps with the currently active certificate.
Downloads the latest federation metadata XML from Azure AD and uploads it to CoreData.
When current Azure AD certificate is about to expire (or any time earlier, after creating a new certificate) System Administrator activates the new certificate and deletes the old one.
CoreData SSO continues working as CoreData already has a metadata file containing the newly activated certificate.
